This is default featured slide 1 title
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
This is default featured slide 2 title
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
This is default featured slide 3 title
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
This is default featured slide 4 title
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
This is default featured slide 5 title
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.This theme is Bloggerized by Lasantha Bandara - Premiumbloggertemplates.com.
Thursday, 5 January 2017
Hire the Right SEO Company for Your Business
Friday, 30 December 2016
How RankBrain Changes Entity Search
Columnist Kristine Schachinger provides a handy primer on entity search, explaining how it works and how Google is using its RankBrain machine learning system to make it better.
- MORE

RankBrain is one of the “hundreds” of signals that go into an algorithm that determines what results appear on a Google search page and where they are ranked, Corrado said. In the few months it has been deployed, RankBrain has become the third-most important signal contributing to the result of a search query, he said.
Hummingbird
Semantic search seeks to improve search accuracy by understanding searcher intent and the contextual meaning of terms as they appear in the searchable dataspace, whether on the Web or within a closed system, to generate more relevant results. Semantic search systems consider various points including context of search, location, intent, variation of words, synonyms, generalized and specialized queries, concept matching and natural language queries to provide relevant search results. Major web search engines like Google and Bing incorporate some elements of semantic search.
The Move From “Strings” to “Things”
[W]e’ve been working on an intelligent model — in geek-speak, a “graph” — that understands real-world entities and their relationships to one another: things, not strings.
How To Fix Your Website When It Gets Hacked?
It's not uncommon for sites - even large ones with lots of protection - to get hacked. Security is a major problem these days. And if your site gets hacked, it can get damaged in a number of ways. You could lose all your data, or lose its ranking due to malicious activity. So while you can take periodic backups, you cannot prevent someone from hacking into your site. The best and most practical thing to do in such an event is to recover your site as fast as possible so that the effect of the attack is neutralized/minimized.
Here are some tips shared by Google for getting your website back on track after it has been hacked.
Clean up malicious scripts
Hackers can target your site for any number of motives. From taking down your website and deleting its content to simply adding backlinks discreetly, there's a lot that can be done. If you notice suspicious content appearing on your website, delete those unnecessary pages immediately. However, don't just stop there.
Hackers will often insert malicious scripts into your HTML and PHP files. These could automatically be creating rogue backlinks or even new pages. Make sure you check your website's source code and see for any malicious PHP or JavaScript code that could be creating such content.
Maintain your CMS
Websites often get hacked due to vulnerabilities in a CMS that get patched with updates. If you're running an older version, your site is more susceptible to attack. Make sure you keep your CMS updated, and use a strong password for login. If possible, enable two-step verification to secure the login process.
www vs. non-www
www and non-www URLs are not the same. http://www.example.com is not the same as http://example.com - the former refers to a sub-domain 'www', whereas the latter is the root of your site. When checking for malicious content, verify the non-www version of your site as hackers often try to hide content in folders that may be overlooked by the webmaster
Other useful security tips
Avoid using FTP when transferring files to your servers. FTP does not encrypt any traffic, including passwords. Instead, use SFTP, which will encrypt everything, including your password, as a protection against eavesdroppers examining network traffic.
Check the permissions on sensitive files like .htaccess. Your hosting provider may be able to assist you if you need help. The .htaccess file can be used to improve and protect your site, but it can also be used for malicious hacks if they are able to gain access to it.
Be vigilant and look for new and unfamiliar users in your administrative panel and any other place where there may be users that can modify your site.
Got any questions? Feel free to leave a new thread in our discussion forum. You can read the post from Google along with a couple case studies here. Good luck (:
Wednesday, 28 December 2016
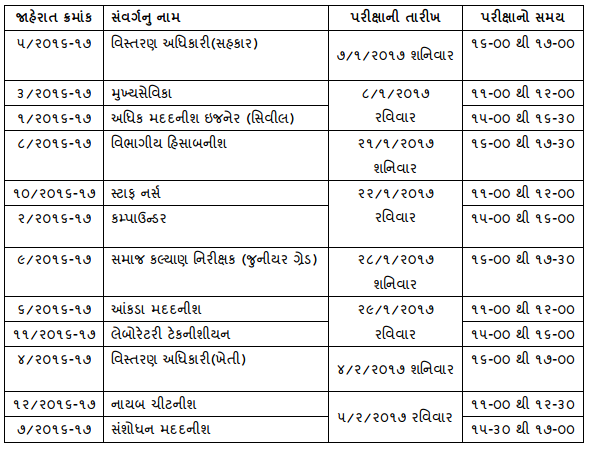
Exam Date Of Talati Cum Mantri And Other Recruitment 2016-2017
Exam Date Of Talati Cum Mantri And Other Recruitment
Monday, 26 December 2016
Chinese carrier enters South China Sea amid renewed tension
The move comes amid renewed tension over self-ruled Taiwan, which Beijing claims as its own, following U.S. President-elect Donald Trump's telephone call with the island's president that upset Beijing.
The ministry said the aircraft carrier the Liaoning, accompanied by five vessels, had early Monday afternoon passed southeast of the Pratas Islands, which are controlled by Taiwan, heading southwest.
The carrier group earlier in the day passed 90 nautical miles south of Taiwan's southernmost point via the Bashi Channel, between Taiwan and the Philippines.
"Staying vigilant and flexible has always been the normal method of maintaining airspace security," said ministry spokesman Chen Chung-chi, declining to say whether Taiwan fighter jets were scrambled or if submarines had been deployed.
Chen said the ministry was continuing to "monitor and grasp the situation".
Senior Taiwan opposition Nationalist lawmaker Johnny Chiang said the Liaoning exercise was China's signal to the United States that it has broken through the "first island chain", an area that includes Japan's Ryukyu Islands and Taiwan.